Quick Start
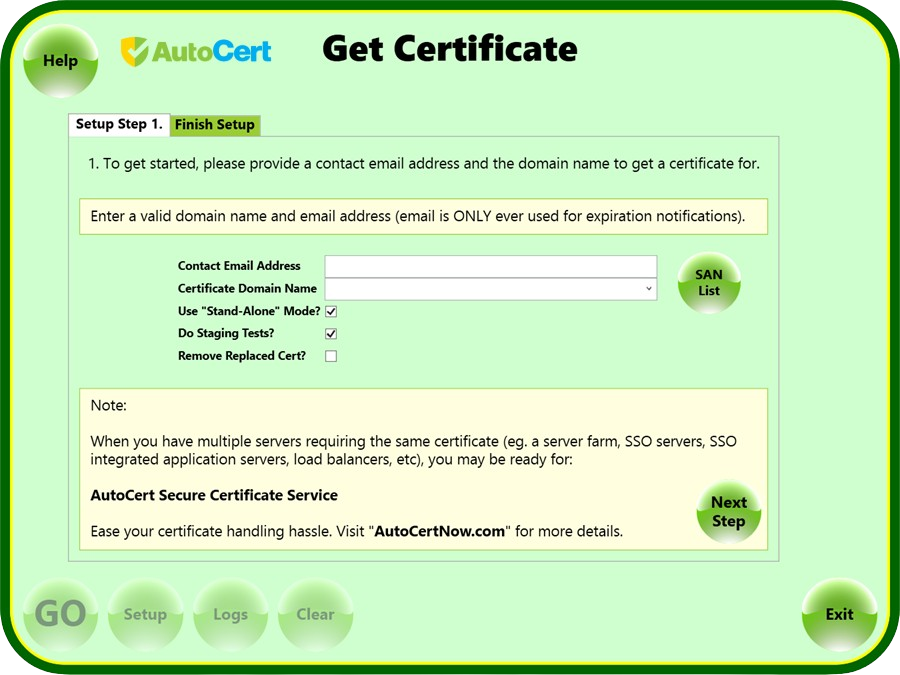
The out-of-the-box behavior of the AutoCert agent (AutoCert.exe) is simple and straightforward. Give it an email address and a domain name and click “GO”. That’s it! (free on GitHub)
Simple AutoCert agent UI.
The goal was to make it as easy as possible for anyone to get the software up and running fast.
Here's a log file showing the typical results after clicking "GO" (or running AutoCert.exe -Auto):